Quantum Secure with Confidence
Making Encrypted Security Part of Your Data Protection is Easy and Affordable
Data security is one of the most pressing issues facing organizations today. Unauthorized access to personal information belonging to employees or customers—Social Security numbers, health records, financial information, even birth dates—can be devastating both to the individuals involved and the company holding the data.
The problem is immense—more than 260 million records have been lost since 2005—and industries, states, and nations have responded by requiring that companies stringently follow best practices for security, including encryption of data. And the costs associated with data breaches are increasing. According to a study by the Ponemon Institute, data breaches now cost organizations an average of $200+ per compromised customer record.
One of the challenges for companies is that products aimed at securing their primary data often don’t work for data sets that are out of their direct control—backup and DR data are especially vulnerable. But encryption solutions can be complex, and can also have some negative implications to data protection strategies, including performance impact.
Quantum’s Perspective
Quantum recommends that IT departments include data encryption as part of their core protection strategy, and can help you integrate the technology easily and cost-effectively into your existing backup, recovery, and archive processes.
End-to-end security solutions help organizations:
- Meet corporate mandates and even legislative requirements to encrypt sensitive data
- Protect your company’s reputation
- Protect against security breaches, whether caused by hard drive removal or by losing tapes
- Take advantage of encryption without sacrificing performance and your ability to meet increasingly demanding SLAs
Solution Details
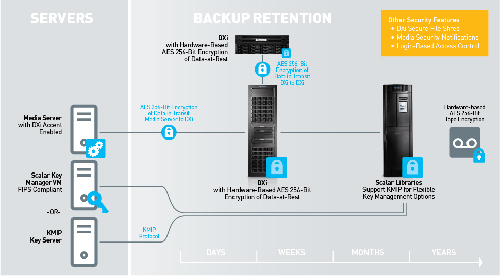
Quantum’s encryption approach features compliance with the most stringent international regulatory and interoperability standards, including FIPS 140-2 (Federal Information Processing Standard 140-2) for data and KMIP (Key Management Interoperability Protocol) and IEEE1619.1 for key management. And because they leverage standards-based, integrated technology and include centralized management, Quantum’s encryption solutions preserve maximum performance, keep costs low, and minimize administrative overhead. Secure all protected data whether it is at rest on local or remote disk backup systems, being transmitted over networks during replication, or stored in tape libraries or on remote DR tapes.
Encryption for DXi Deduplication Series
The DXi®-Series of deduplication appliances supports a variety of security features including:
- Self-Encrypting Drives. With AES 256-bit government grade encryption that is performed by the drives, there is no performance impact.
- Secure Replication. When replicating deduplicated data between DXis, the replicated data can be encrypted using the AES 256-bit algorithm to encrypt data-in-flight over the LAN or WAN.
- Secure File Shred. DXi gives customers the ability to securely delete specific backup images that have been inadvertently written to a DXi.
- DXi Accent™ reduces network bandwidth usage by performing deduplication on the media server before sending that data to a DXi. DXi Accent is optimized for use over the WAN, and is capable of working around WAN latencies for use at remote sites. But DXi Accent isn’t just for WANs, it provides benefits in congested LAN environments and VM hosts as well. DXi Accent leverages the Symantec OST protocol, is part of Quantum’s OST plug-in, and is supported with Symantec NetBackup on Windows and Linux operating systems, and with Symantec BackupExec on Windows operating systems.
Encryption For Scalar Tape Libraries
Scalar® libraries support LTO-based tape encryption and a variety of key management options:
- Encryption is performed by the tape drive so there is no performance impact, and the drives use a robust AES 256-bit algorithm.
- Scalar Key Manager is a FIPS 140-2 Level 1-compliant, scalable key management solution that supports the entire Scalar library portfolio. It is simple to deploy as either an appliance or as a virtual machine.
- Scalar libraries support the Key Management Interoperability Protocol 1.0 (KMIP 1.0) standard for exchanging encryption keys over the network. This support gives customers the flexibility to deploy a single key management system to manage their encryption keys for various devices in their data center. In addition to the Scalar Key Manager, Quantum’s Scalar libraries are compatible with SafeNet KeySecure key servers, with plans to support other KMIP-compliant key servers in the future.
- Where application-based key management is desired, Scalar libraries support the IEEE 1619.1 for industry-standard in-band key management.
Quantum data protection products all provide Login-Based Access Control, and also provide other means of access control such as preventing unintended hosts from having access to specific devices on the SAN.